Hugo Huang
on 24 June 2022
Weave Cybersecurity into your product design
How important security is for your application and digital services? “Very important”, this is the answer we get the most often from Product Managers and Executives. Nobody wants the malware to take advantage of the vulnerabilities of their applications. However, any access point to the internet can be an entry point for hackers. Considering the ubiquitous awareness of the importance and risks associated with security, you may expect that security has been well embedded in all the aspects of digital product development, especially in the early stages of product design when costs are comparatively manageable.
Unfortunately, according to a recent study by MIT, “cybersecurity is rarely considered among the criteria in the early design phase”. This study finds three reasons why this ignorance of cyber security happens in the early stages:
- Cybersecurity doesn’t directly contribute to revenue.
- Cybersecurity can potentially delay time to market.
- Designers and managers typically underestimate how severe the consequences of cybersecurity vulnerabilities can be.
All of these three arguments are self-explanatory. First, in most cases, customers pay for the features of your products, while many customers consider security as a benchmark or a guarantee at the best. They may willing to pay the premium for a higher security service level, but they can hardly quantify their willingness to pay. On the contrary, there are multiple pricing tools for you to evaluate most of the product features, such as Conjoint Analysis, Contingent Valuation, and Economic Value to the Customer. So the value of cybersecurity doesn’t show up spontaneously. Second, cybersecurity designs are not free. They require resources, from Cloud Infrastructure to hands-on expertise. You may also need dedicated training to implement those designs. That being said, your product may need more time to get ready to be launched. Finally, more and more ransomware cases teach us that the security vulnerabilities may be worth more than you thought when they are in bad people’s hands. Can you imagine Colonial Pipeline spending $5 Million for cybersecurity on day 1 of IT system development? But they did pay $5 Million when they are under attack.
How to solve this dilemma?
The answer is to weave cybersecurity into your product design. Make cybersecurity one of the basic design criteria. Does this require deeper knowledge about multiple security considerations? Yes. Will the developing team incur a higher cost or steeper learning curve once they weave cybersecurity into product design? Not exactly. You can simply start from a security development environment, such as Ubuntu Pro for Google Cloud.
Ubuntu Pro enables your cybersecurity capabilities and keeps your budget under control. Its key features include:
Predictable lifecycle
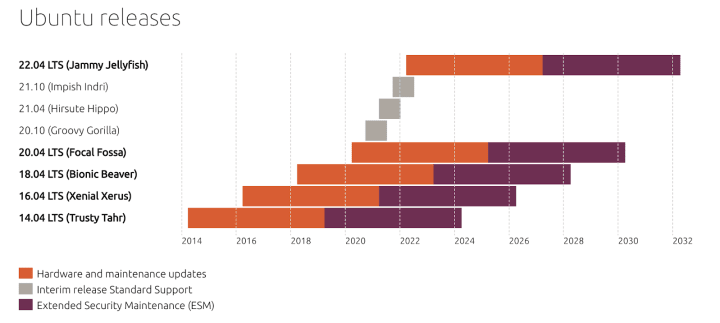
Every two years, Ubuntu Pro will be released at Google Cloud at the same time as Ubuntu LTS published. It will be well maintained for the next ten years.
Certified Compliance & hardening
Regulatory requirements are complex. However, Ubuntu Pro provides a simple command “ua enable” that helps you configure a compliant environment, including FIPS 140-2, CIS, Common Criteria, and STIG,

Vulnerability Management
Ubuntu Pro fully integrates the Canonical OVAL database, which is used to evaluate and manage security risks related to any existing Ubuntu components. Through Google Cloud VM manager, you will be able to check if your virtual machine has any vulnerabilities.

The earlier you build cybersecurity in your product development, the more effective the whole product development process will be. A secure development environment would be the best starting point for you to face cybersecurity challenges. It avoids the additional work, extra costs, and disrupted time-to-market cycle. Now, start developing your next product in Ubuntu Pro for Google Cloud.



